PANDA - Precise Attack Detection for Network Domains by Application Classification

Institutions
- TU Berlin
- BTU Cottbus
Team @ TKN
Funding
- DFG (Deutsche Forschungsgemeinschaft)
Project Time
- 12/2019 - 12/2022
Description
The detection of attacks on large administrative network domains, e.g., an enterprise network consisting of multiple subnets, is nowadays usually accomplished centrally by analyzing the data traffic on the uplink to the Internet. This allows detecting attacks from the Internet, but has substantial disadvantages. Insider attacks cannot be detected, no matter if they are initiated deliberately or triggered by compromised (private) devices. A network-wide distributed monitoring would be a useful alternative to established procedures, but it faces a number of still unsolved problems:
- Data rates in the subnets are sporadically very high and often highly variable (e.g., load peaks of up to 10 Gbit/s).
- High data rates along with the standard configurations typically used for monitoring usually imply high false alarm rates.
- Data traffic is increasingly encrypted and eludes traditional analysis methods.
- The increased deployment of virtualization technologies, such as virtual machines and networks, establishes areas that are inaccessible for monitoring measures.
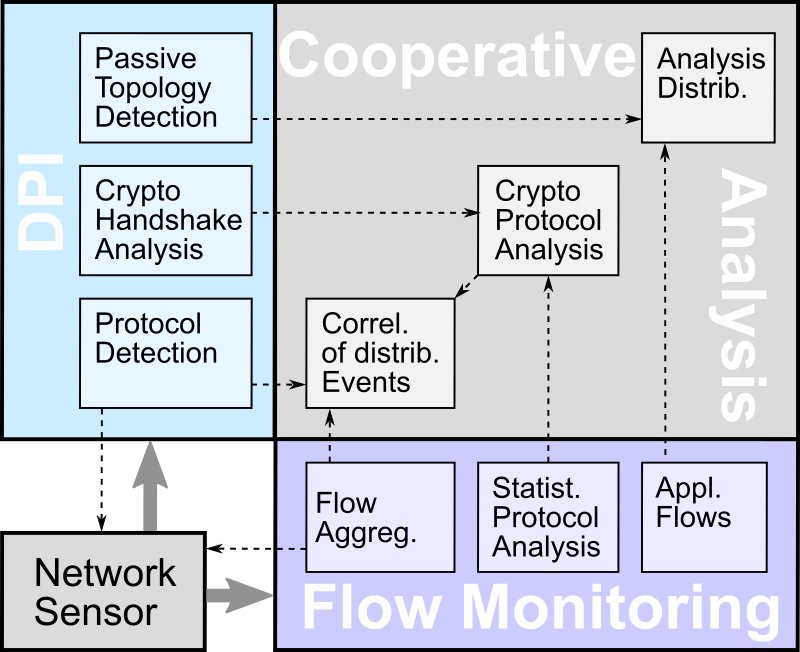
When performing security monitoring usually flow aggregation and deep packet inspection (DPI) are carried out separately. Flow analysis so far considers only accounting information up to the transport layer. New technologies, such as virtual networks, dilute transport layer information resulting from flow aggregation because same IP addresses now represent different systems. In addition, new protocols, such as HTTP/2, further complicate the analysis process because additional context is often missing, e.g., single connection or multiplexing. Likewise, the DPI often runs into the void, since there is no contextual information regarding the observed application.
In the proposed research project, the methods of flow aggregation and DPI will be used complementarily. Key aspects of the investigations are a significant reduction of the data volume to be analyzed at the network sensor, the examination of alarm relevance, the monitoring of data flows also in virtual environments, analyses of cryptographic traffic to infer supported applications and applied protocols, and methods for cooperative analysis within the administrative domain. Problems to be solved include an accurate identification of applications (including observed protocol dialects, if distinguishable) providing context for the DPI to allow a dynamic adaptation of the signature bases to the context, an efficient aggregation of security information from the application layer to AppFlows to allow analysis relocations, the aggregation of information beneath the network layer to enable the integration of virtual systems into the monitoring, and the extraction of parameters from initiating handshakes during connection establishment of encrypted channels to detect vulnerabilities raised by outdated crypto methods.
Selected Publications
2023
Conferences and Workshops
 Hossein Doroud, Tobias Wiese, Felix Erlacher and Falko Dressler, "Work Balancing vs. Load Balancing for Network IDS Parallelization," Proceedings of 19th IEEE International Conference on Wireless and Mobile Computing (IWCMC 2023), Marrakesh, Morocco, June 2023, pp. 488–493.
[DOI, BibTeX, PDF, More details]
Hossein Doroud, Tobias Wiese, Felix Erlacher and Falko Dressler, "Work Balancing vs. Load Balancing for Network IDS Parallelization," Proceedings of 19th IEEE International Conference on Wireless and Mobile Computing (IWCMC 2023), Marrakesh, Morocco, June 2023, pp. 488–493.
[DOI, BibTeX, PDF, More details] Hossein Doroud, Omar Alkhateeb, Elnaz Alizadeh Jarchlo and Falko Dressler, "L-IDS: A Lifelong Learning Approach for Intrusion Detection," Proceedings of 19th IEEE International Conference on Wireless and Mobile Computing (IWCMC 2023), Marrakesh, Morocco, June 2023, pp. 482–487.
[DOI, BibTeX, PDF, More details]
Hossein Doroud, Omar Alkhateeb, Elnaz Alizadeh Jarchlo and Falko Dressler, "L-IDS: A Lifelong Learning Approach for Intrusion Detection," Proceedings of 19th IEEE International Conference on Wireless and Mobile Computing (IWCMC 2023), Marrakesh, Morocco, June 2023, pp. 482–487.
[DOI, BibTeX, PDF, More details]
2022
Journals and Magazines
 Felix Erlacher and Falko Dressler, "On High-Speed Flow-based Intrusion Detection using Snort-compatible Signatures," IEEE Transactions on Dependable and Secure Computing, vol. 19 (1), pp. 495–506, January 2022.
[DOI, BibTeX, PDF, More details]
Felix Erlacher and Falko Dressler, "On High-Speed Flow-based Intrusion Detection using Snort-compatible Signatures," IEEE Transactions on Dependable and Secure Computing, vol. 19 (1), pp. 495–506, January 2022.
[DOI, BibTeX, PDF, More details]
Conferences and Workshops
 Hossein Doroud, Ahmad Alaswad and Falko Dressler, "Encrypted Traffic Detection: Beyond the Port Number Era," Proceedings of 47th IEEE Conference on Local Computer Networks (LCN 2022), Edmonton, Canada, September 2022, pp. 198–204.
[DOI, BibTeX, PDF, More details]
Hossein Doroud, Ahmad Alaswad and Falko Dressler, "Encrypted Traffic Detection: Beyond the Port Number Era," Proceedings of 47th IEEE Conference on Local Computer Networks (LCN 2022), Edmonton, Canada, September 2022, pp. 198–204.
[DOI, BibTeX, PDF, More details]
Technical Reports and Regional Workshops
- Hossein Doroud, Tobias Wiese, Felix Erlacher and Falko Dressler, "Work Balancing vs. Load Balancing in Network Ids Parallelization," SSRN, Preprint, 4070543, March 2022. [DOI, BibTeX, More details]